
The secure AI operating system for real work
Run automation in a sandboxed runtime with explicit permissions, structured tools, and full auditability. No surprise access. No hidden side effects.
- WASM sandboxed packs — no raw filesystem or network access.
- Explicit permissions per pack, enforced at runtime.
- Structured tool calls with schema validation.
- Secrets stored in the OS keychain, not config files.
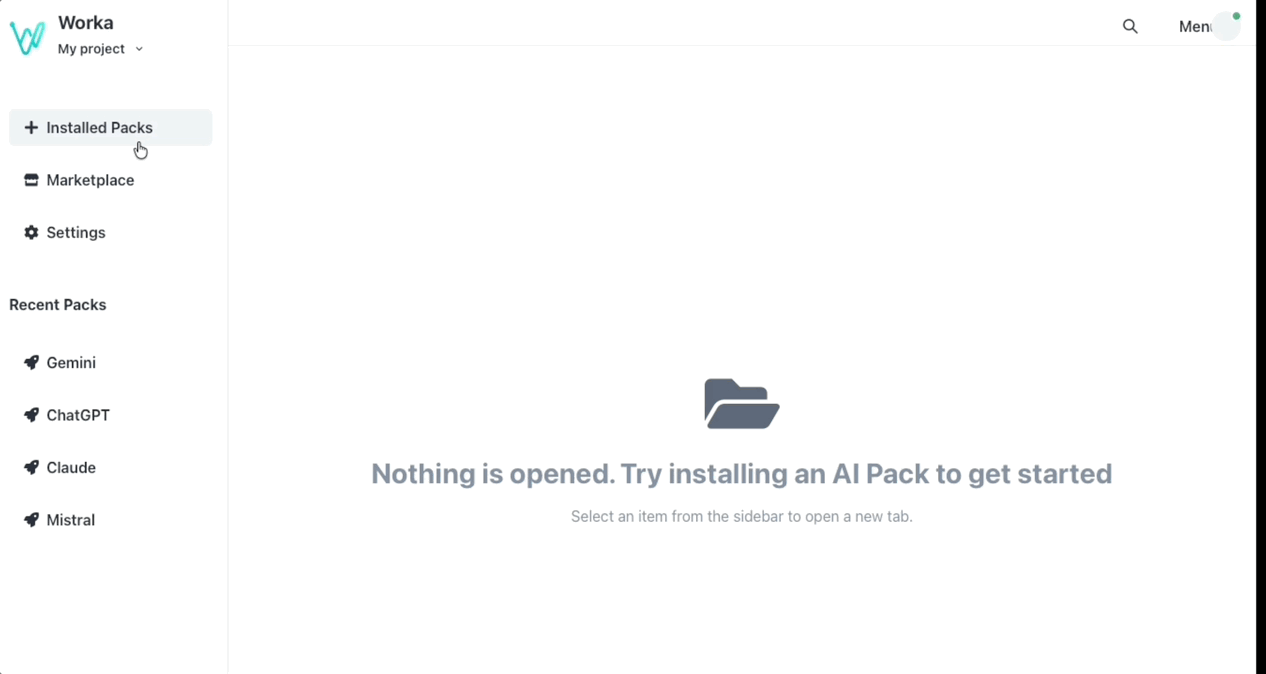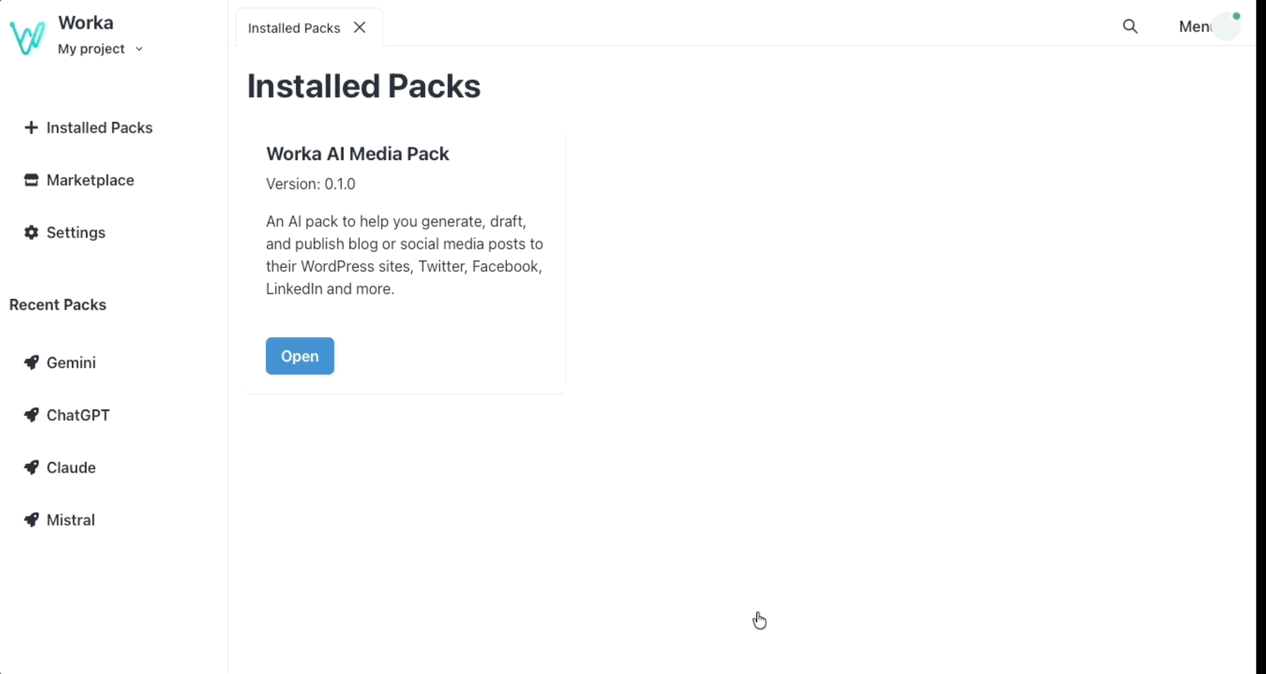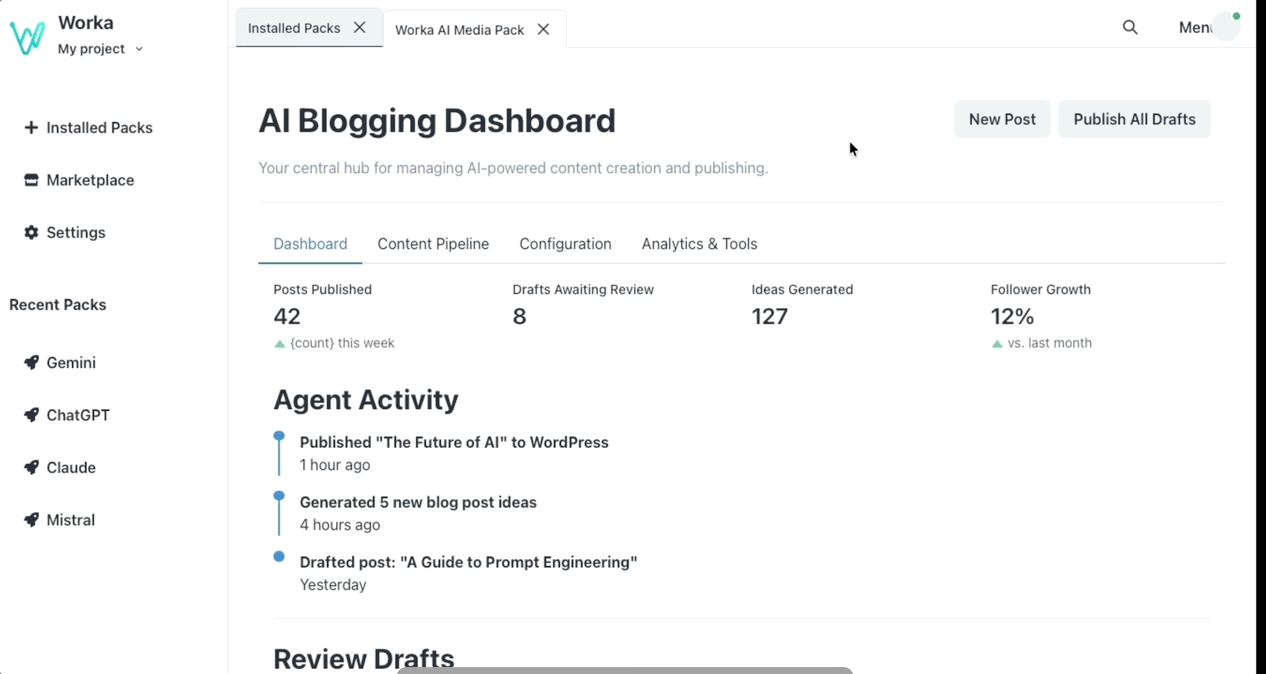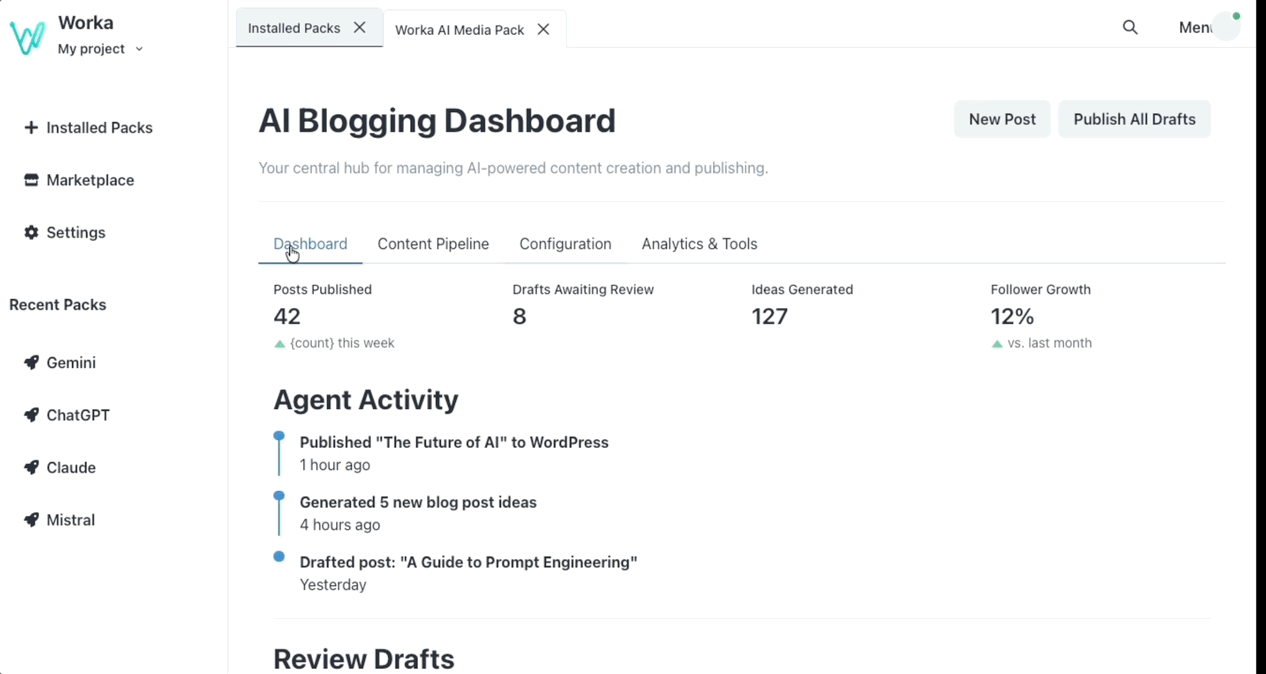
Meet Worka
Worka is the secure AI operating system that runs trusted workflows
locally, with explicit permissions, structured tools, and complete auditability.
It is designed for production environments where you need predictable outcomes, strong boundaries, and a clear record of every action taken.
Sandboxed packs with explicit permissions
Packs run in a locked-down runtime. No raw filesystem or network access unless you grant it.
Installable AI packs (.aip)
One-click install automation bundles. Dependencies are enforced. Capabilities are declared.
Secrets stored in OS keychain
Credentials live in the system vault, not in config files. You stay in control.
Audit trails for every action
Structured workflows with step-by-step logs so you can verify exactly what happened.
Structured UI surfaces (A2UI)
Packs render trusted UI views for operators and teams, not just text responses.
Attribution and accountability
Every action is tied to a pack, workflow, and actor for traceability.
How Worka stays safe
Worka treats AI output as untrusted input and validates every action at runtime.
Pack declares capabilities
Every pack lists the permissions it needs before it can run.
Host enforces boundaries
Sandboxed WASM runtime enforces permissions and dependency allowlists.
Tools are validated
All tool calls are schema‑validated to prevent unsafe execution.
Actions are audited
Every step is recorded, so you can verify outcomes and trace issues.
Security by design
Worka is built for real operations, not unsafe demos. Every workflow is sandboxed, permissioned, and auditable — so automation stays reliable as it scales.
Default behavior is deny‑by‑default. Packs only get what they explicitly request, and tool calls are validated before execution.
WASM sandbox runtime
Every pack runs inside a WebAssembly sandbox with a strict capability boundary. There is no ambient file or network access.
Explicit permissions
Packs declare their capabilities up front. The host enforces those permissions at runtime, not via best effort.
Structured tools, validated inputs
Tool calls are schema‑validated. Untrusted LLM output cannot execute arbitrary actions.
Dependency allowlists
A pack can only call other packs it explicitly depends on. Everything else is denied by default.
OS‑level secrets storage
Credentials are stored in the system keychain. Nothing in plaintext config files.
Complete audit trail
Every step is logged and traceable. You can review what happened, when, and why.
- Explicit permission grants for filesystem, network, and device access.
- Schema‑validated tools — no arbitrary code execution from LLM output.
- Every workflow is logged with inputs, outputs, and status transitions.
- Pack dependencies are enforced and isolated from each other.
Trust guarantees
These are hard constraints in Worka’s architecture — not optional settings.
- No raw filesystem access by default
- No raw network access by default
- Secrets stored in OS keychain
- Schema‑validated tool inputs
- Pack dependencies strictly enforced
- Every action is auditable
- Core runtime written in Rust (memory‑safe)
- WhatsApp via official API (account‑safe)
The Pack Model
Worka packs are isolated automation modules designed for safety, traceability, and reliable execution across desktop and mobile.
Declarative capabilities
Each pack declares the exact permissions it needs before execution.
Strict dependency graph
A pack can only call other packs it explicitly depends on.
Structured UI (A2UI)
Packs render trusted UI views with deterministic structures.
Portable & audited
Packs are versioned artifacts with clear provenance and logs.
Runs everywhere, safely
Worka’s WASM runtime brings the same guarantees to desktop and mobile — no matter where your workflows run.
Desktop
Run packs locally with the same safety guarantees across macOS, Windows, and Linux.
Mobile
WASM makes native execution possible without unsafe gateways or fragile runtimes.
Cloud (optional)
Use cloud APIs only where needed — never as a requirement for third‑party packs.
Worka for Everyone
Built for people who need automation they can trust
Worka is not a generic chatbot. It is an operating system for safe AI workflows — designed to reduce risk, not create it.
Operators
Run repeatable workflows with audit trails, approvals, and clear accountability.
Security Teams
Zero‑trust defaults, explicit capabilities, and verifiable execution.
Developers
Build packs with strict schemas, minimal permissions, and predictable behavior.
Install Worka
Get the app for macOS, Windows, or Linux
Add a pack
Install .aip packs from a trusted registry with declared capabilities
Grant permissions
Approve capabilities explicitly, per pack and per workflow
Audit outcomes
Track every step, verify results, and troubleshoot quickly
What You Can Automate
Real workflows that demand accountability, not guesswork
Worka is built for operational clarity: every step is deterministic, reviewable, and tied back to the pack that executed it.
Property Operations
Coordinate tenants, contractors, and inspections with a full audit trail.
Secure Messaging Automation
Route tenant and vendor messages through verified workflows, not ad‑hoc prompts.
Compliance & Reporting
Generate checklists and reports with structured outputs and approvals.
System Workflows
Automate internal ops with explicit permissions and step-by-step logs.
Escalations & Approvals
Require human approval for sensitive actions, with full visibility.
Trusted Documentation
Produce consistent, verifiable artifacts instead of brittle chat outputs.
Become a Partner
Build secure .aip packs with explicit permissions and structured tools. Package your automation expertise into reusable workflows you can trust.
Become a PartnerLaunching with a trusted pack ecosystem
A curated registry of secure, audited packs for real operations
For Developers
Build packs with strict schemas, explicit dependencies, and zero‑trust defaults. Ship workflows that run locally and remain fully auditable.